https://blog.securityps.com/2013/06/session-fixation-forms-authentication.html
https://stackoverflow.com/questions/23758704/asp-net-sessionid-vs-aspxauth-why-do-we-need-both-of-them
chatgpt:
Remember that while Session can be a convenient way to store temporary user-specific data, you should be cautious about what data you store in session, as it can affect application performance and scalability. Additionally, always secure sensitive actions using proper authentication and authorization mechanisms, such as [Authorize].
User
But isn't it possible than instead of Authorize I could check if a particular data in session exists say, I could store user's role, and userid in session when he logs in. So I could skip [Authorize] and just make use of session data?
ChatGPT
While it's technically possible to use session data to implement a simple form of authorization, it's generally not recommended for several reasons:
Security Concerns:
Session data is stored on the server, and if not properly secured, it could be vulnerable to session hijacking or other security exploits. The [Authorize] attribute, on the other hand, is a built-in and well-tested mechanism that is specifically designed for authentication and authorization.
Code Maintainability:
The [Authorize] attribute provides a clear and standardized way to handle authentication and authorization. It keeps the authorization logic centralized and easy to understand. Relying on scattered checks for session data across your codebase can make the code less maintainable and more error-prone.
Flexibility:
The [Authorize] attribute supports various authentication and authorization schemes, including role-based authorization and custom policies. It provides a flexible and extensible framework that can be easily adapted to different scenarios. Relying solely on session data might limit your ability to implement more advanced authorization requirements.
Consistency:
Using [Authorize] promotes consistency in your application. Developers working on the project will expect to see this attribute for controlling access to actions and controllers. Relying on session data for authorization breaks this consistency.
While you could use session data for a basic form of authorization, it's advisable to use [Authorize] for handling authentication and authorization in a standardized and secure manner. If you have specific requirements that are not easily met by the built-in authorization mechanisms, consider extending the authorization system using custom policies or other extensibility points provided by ASP.NET MVC. This approach will lead to more maintainable and secure code in the long run.
User
"ession data is stored on the server, and if not properly secured, it could be vulnerable to session hijacking or other security exploits. "
How??
ChatGPT
Session data is stored on the server, and the server maintains a session identifier (session ID) for each user. When a user logs in, the server generates a unique session ID and associates it with the user's session data. This session ID is typically stored in a cookie on the user's browser and sent with each subsequent request, allowing the server to identify and retrieve the corresponding session data.
If session data is not properly secured, several security vulnerabilities can arise, including session hijacking:
Session ID Prediction:
If session IDs are predictable or easily guessable, an attacker could potentially predict a valid session ID and impersonate another user. This can happen if the session ID is generated using insufficiently random or easily guessable algorithms.
Session ID Theft:
If an attacker gains access to a user's session ID, perhaps through techniques like session sniffing, cross-site scripting (XSS), or other security vulnerabilities, they can impersonate the user by presenting the stolen session ID. This is known as session theft.
Session Fixation:
In a session fixation attack, an attacker tricks a user into using a specific session ID. For example, the attacker might send the user a link containing a valid session ID. When the user clicks the link, the attacker can then use that session ID to impersonate the user.
To mitigate these risks and enhance session security, it's crucial to follow best practices:
Use Strong Session IDs: Ensure that session IDs are generated using strong randomization techniques, making them difficult to predict.
Secure Transmission: Always use HTTPS to encrypt data transmitted between the server and the client, preventing session sniffing attacks.
Protect Against Cross-Site Scripting (XSS): Implement measures to mitigate the risk of XSS attacks, as they can be used to steal session IDs.
Implement Session Timeout: Set a reasonable session timeout to limit the window of opportunity for attackers to exploit stolen session IDs.
Regenerate Session IDs: When a user logs in or experiences a significant change in privilege, regenerate the session ID to mitigate session fixation attacks.
Store Session Data Securely: If session data is sensitive, encrypt it or avoid storing sensitive information in the session altogether.
By addressing these concerns and following best practices, developers can enhance the security of session management in web applications. Additionally, frameworks like ASP.NET often provide built-in mechanisms for secure session management when configured correctly.
User
so if I understand correct, In the asp.net mvc 5, the server when a user logs in creates a cookie in which it stores the session ID. And this cookie is sent on each HTTP Request from the browser as an Idenitfier. Now, the attacker, if in some way is able to get his hands on the session cookie, can just copy the session cookie and start sending request with the victim user's cookie. Am I correct?
ChatGPT
Yes, you have a correct understanding of the basic mechanics of session management and the potential risks associated with session cookie theft. Here's a more detailed breakdown:
User Login:
When a user logs in, the server generates a unique session ID and associates it with the user's session data.
This session ID is often stored in a cookie, commonly referred to as the session cookie.
Session Cookie:
The session cookie is then sent with each subsequent HTTP request made by the user's browser to the server.
It serves as an identifier, allowing the server to recognize and associate the incoming requests with the correct user session.
Attacker Access:
If an attacker somehow gains access to the session cookie (through techniques like session sniffing, cross-site scripting, etc.), they could effectively impersonate the user by presenting the stolen session cookie in their own requests.
Session Hijacking:
With the stolen session cookie, the attacker can perform actions on behalf of the victim user until the session expires or is otherwise invalidated.
Mitigations:
To mitigate the risk of session hijacking, it's crucial to follow best practices, as mentioned in the previous response. These include using strong session IDs, securing transmission with HTTPS, protecting against cross-site scripting, and implementing session timeout strategies.
It's important to note that while session cookies are a common method for maintaining user sessions, the security of the overall system depends on a combination of factors, including the strength of session ID generation, the implementation of secure transmission, and the prevention of common web application vulnerabilities. Regularly auditing and updating security measures is crucial to maintaining a secure web application.
User
but how does [Authorize] helps in this, that Session data doesn't?
ChatGPT
The [Authorize] attribute in ASP.NET MVC serves as a mechanism for enforcing authentication and authorization at the controller or action level. It works in conjunction with the authentication system and user identity to ensure that only authenticated users with the appropriate roles or claims can access certain parts of an application.
Here's how [Authorize] helps enhance security compared to relying solely on session data:
Authentication Check:
[Authorize] explicitly checks whether a user is authenticated before allowing access to a controller or action. This is more robust than relying on session data alone because session data can be manipulated or spoofed if not properly secured.
Centralized Authorization Logic:
The [Authorize] attribute allows you to centralize authorization logic. You can specify role requirements, custom policies, or other conditions directly at the controller or action level, making it easier to manage and understand the access control rules in your application.
Integration with Authentication Middleware:
[Authorize] integrates seamlessly with the ASP.NET authentication middleware. This middleware handles various aspects of user authentication, including cookie authentication (common for session management) and other authentication schemes. It provides a standardized way to authenticate and authorize users.
Role-Based Authorization:
[Authorize] supports role-based authorization, allowing you to specify that only users with certain roles can access a particular resource. This adds an extra layer of security beyond simple authentication.
Here's an example of using [Authorize] to restrict access to a controller:
csharp
Copy code
[Authorize(Roles = "Admin")]
public class AdminController : Controller
{
// Actions in this controller can only be accessed by users in the "Admin" role.
}
By using [Authorize], you're leveraging a built-in and well-tested framework for controlling access to different parts of your application based on user authentication and authorization. It complements session management, which is more focused on persisting user-specific data across requests.
In summary, while session data is valuable for maintaining user state, [Authorize] is a crucial tool for enforcing access control policies, checking user authentication status, and ensuring that users have the necessary roles or claims to access specific resources in your application. Together, they contribute to a more comprehensive and secure web application.
User
but say if I copy the cookie which has the session ID of the logged in User.
How would [Authorize] prevent me from accessing the resource/action?
ChatGPT
The [Authorize] attribute alone won't prevent an attacker who has stolen a valid session cookie from accessing a resource or action. The primary purpose of [Authorize] is to ensure that the user making the request is authenticated and possesses the required roles or claims, based on the authentication mechanism in use.
If an attacker has a valid session cookie, they could include that session cookie in their HTTP requests and potentially gain access to actions or resources protected by [Authorize] if the associated user has the required roles or claims.
However, there are additional security measures and best practices that can be employed to mitigate the risks associated with stolen session cookies:
Session Timeout:
Implement a reasonable session timeout. If a session remains inactive for a specified period, it should expire, reducing the window of opportunity for an attacker to use a stolen session cookie.
Session Regeneration:
Regenerate the session ID upon significant events, such as user authentication or privilege changes. This can help mitigate session fixation attacks.
Secure Transmission:
Always use HTTPS to secure the transmission of session cookies between the client and the server, reducing the likelihood of session sniffing.
IP Checking:
Implement IP address checking as an additional layer of security. If the session suddenly switches to a different IP address, it might indicate a potential attack.
Token-Based Authentication:
Consider using token-based authentication mechanisms (like JSON Web Tokens) that can include additional information and be more resistant to certain types of attacks compared to session cookies.
Logging and Monitoring:
Implement logging and monitoring to detect unusual activity, such as multiple login attempts from different locations.
It's important to note that while [Authorize] focuses on the authorization aspect, ensuring the user has the necessary roles or claims, preventing unauthorized access in the case of a stolen session cookie involves a combination of factors, including secure session management practices and other security mechanisms. Security is a multi-layered approach, and no single measure can provide absolute protection.
User
"Therefore, the [Authorize] attribute will redirect you to the login page, even if you have the cookie with the session ID of the logged-in user."
Why though? What special thing does that attrbute checks? Doesn't it check the cookie as well? So?
ChatGPT
The [Authorize] attribute in ASP.NET MVC primarily checks for the presence of a valid authentication ticket, not directly the session cookie. Here's how it generally works:
Authentication Ticket:
When a user logs in, the authentication system creates an authentication ticket. This ticket typically contains information about the user, such as their username, roles, and other claims.
This ticket is then encrypted and usually stored in a cookie, often referred to as an authentication cookie.
Authorization Check:
The [Authorize] attribute checks for the existence of a valid authentication ticket. If the user has a valid authentication ticket, it indicates that they have been authenticated.
Redirect to Login Page:
If the user is not authenticated (i.e., no valid authentication ticket is present), the [Authorize] attribute redirects the user to the login page.
The idea is that only authenticated users should be allowed access to actions or resources decorated with [Authorize].
Separate Concerns:
Authentication and session management are somewhat separate concerns in ASP.NET. While session management often involves a session cookie, authentication relies on the presence of a valid authentication ticket.
Even if an attacker has a session cookie, they would still need the corresponding valid authentication ticket to pass the [Authorize] check.
In summary, the [Authorize] attribute checks for the presence of a valid authentication ticket, which is typically stored in a cookie. If the user doesn't have a valid authentication ticket (meaning they are not authenticated), they are redirected to the login page. This helps to enforce the principle that only authenticated users should have access to specific resources or actions in your application.
User
Oh so you mean there are 2 cookies? One is having Auhtentication Ticket and one is storing session Id?
ChatGPT
Yes, that's correct. In many ASP.NET applications, especially those that use the Forms Authentication system or ASP.NET Core Identity, there are often two distinct cookies involved:
Authentication Cookie (Ticket):
This cookie contains the user's authentication ticket, which includes information about the user's identity, roles, and any additional claims.
It is encrypted and sent to the user's browser. The browser then includes this cookie with each subsequent HTTP request to the server.
The presence of a valid authentication cookie indicates that the user is authenticated.
Session Cookie:
This cookie is related to session management and is distinct from the authentication cookie.
It is used to maintain user-specific data across multiple requests. The session cookie typically contains a session ID, and the server associates this ID with the user's session data on the server side.
The session cookie is often used for non-sensitive, temporary data storage (e.g., user preferences, shopping cart contents).
These two cookies serve different purposes:
The authentication cookie is crucial for determining whether a user is authenticated and, if so, who they are. It plays a central role in the authorization process, including checks performed by the [Authorize] attribute.
The session cookie is more focused on maintaining user-specific data across requests. It is used for managing the user's session state.
Both cookies contribute to the overall functionality and security of a web application, but they are distinct and serve different roles in the authentication and session management processes.
User
so say I am using FormAuthentication, then there is one cookie for that and one cookie for SessionID storage?
ChatGPT
Yes, that's correct. When using Forms Authentication in ASP.NET, typically there will be one cookie for authentication and another for session management. Here's a breakdown:
Forms Authentication Cookie:
This cookie contains the user's authentication ticket, which includes information about the user's identity, roles, and any additional claims.
It is encrypted and sent to the user's browser. The browser then includes this cookie with each subsequent HTTP request to the server.
The presence of a valid forms authentication cookie indicates that the user is authenticated.
Session Cookie:
This cookie is related to session management and is distinct from the forms authentication cookie.
It is used to maintain user-specific data across multiple requests. The session cookie typically contains a session ID, and the server associates this ID with the user's session data on the server side.
The session cookie is often used for non-sensitive, temporary data storage (e.g., user preferences, shopping cart contents).
So, in the context of Forms Authentication, there are usually these two separate cookies working together to manage user authentication and session state. The forms authentication cookie handles the user's identity and authorization, while the session cookie handles the storage of temporary session-specific data.
User
so how many cookies are really created?
ChatGPT
The number of cookies created in an ASP.NET application can vary based on the specific features and configurations used. However, in a typical scenario using Forms Authentication, there are often two cookies involved:
Forms Authentication Cookie:
This cookie contains the user's authentication ticket, which includes information about the user's identity, roles, and any additional claims.
It is encrypted and sent to the user's browser. The browser then includes this cookie with each subsequent HTTP request to the server.
This cookie is used for user authentication and authorization.
Session Cookie:
This cookie is related to session management and is distinct from the forms authentication cookie.
It is used to maintain user-specific data across multiple requests. The session cookie typically contains a session ID, and the server associates this ID with the user's session data on the server side.
This cookie is used for managing the user's session state, including temporary data storage.
In summary, while there might be other cookies related to application features or third-party components, a common scenario involves two main cookies: one for Forms Authentication (user authentication) and another for session management. Keep in mind that specific implementations and configurations might lead to variations in cookie usage.
User
so if someone steals ASP.NET_SessionId and I have not used [Authorize] in my actions. They would easily be able to access the resources/actions?
But if I use [Authorize] it will also check authentication cookie ticket that is .ASPXAUTH s cookie and hence won't allow the access?
Am I CORRECT?
ChatGPT
Yes, you are correct. Let's break down the scenarios:
Scenario 1: No [Authorize] Attribute Used
If an attacker steals the ASP.NET_SessionId cookie and your actions do not have the [Authorize] attribute applied, they could potentially use the stolen session ID to impersonate the user and access resources/actions. The ASP.NET_SessionId cookie is primarily for session management, and without specific authorization checks, an authenticated user with a valid session ID could potentially access various parts of your application.
Scenario 2: [Authorize] Attribute Used
If you use the [Authorize] attribute on your actions or controllers, the framework checks for the presence of a valid authentication ticket (usually stored in the .ASPXAUTH cookie). Even if an attacker has stolen the ASP.NET_SessionId cookie, they would still need the corresponding valid authentication ticket to pass the [Authorize] check.
The [Authorize] attribute ensures that only authenticated users, with a valid authentication ticket, are allowed access to the specified resources/actions. It adds an additional layer of security by explicitly checking for authentication status and, if configured, specific roles or claims.
In summary, using the [Authorize] attribute provides an additional layer of security by enforcing authentication checks at the action or controller level. Even if an attacker has stolen the session ID cookie, they would need the associated authentication ticket to pass the authorization check imposed by [Authorize]. It's a good practice to use both session management (e.g., ASP.NET_SessionId) and authentication checks (e.g., [Authorize]) to enhance the overall security of your ASP.NET application.
Perplexity:
tell me some Oxford very short introductions that Vsauce would use
Vsauce is a popular YouTube channel that explores a wide range of topics, from science and technology to philosophy and culture. The Oxford Very Short Introductions series offers concise and original introductions to a wide range of subjects that Vsauce might find interesting. Here are some examples of Very Short Introductions that Vsauce might use:- Quantum Theory: A Very Short Introduction by John Polkinghorne
- Relativity: A Very Short Introduction by Russell Stannard
- Astrophysics: A Very Short Introduction by James Binney
- Artificial Intelligence: A Very Short Introduction by Margaret Boden
- The Brain: A Very Short Introduction by Michael O'Shea
- The Universe: A Very Short Introduction by John Gribbin
These introductions provide a thought-provoking and serious introduction to a wide range of subject areas that authors are experts in the field. They not only provide the big picture to a subject but also the texture so you see the debates, the people in it, the new ideas, and the details or nuances you need to develop your knowledge. I want to create a workflow using microsoft word, how to use the shapes for the flowchart?
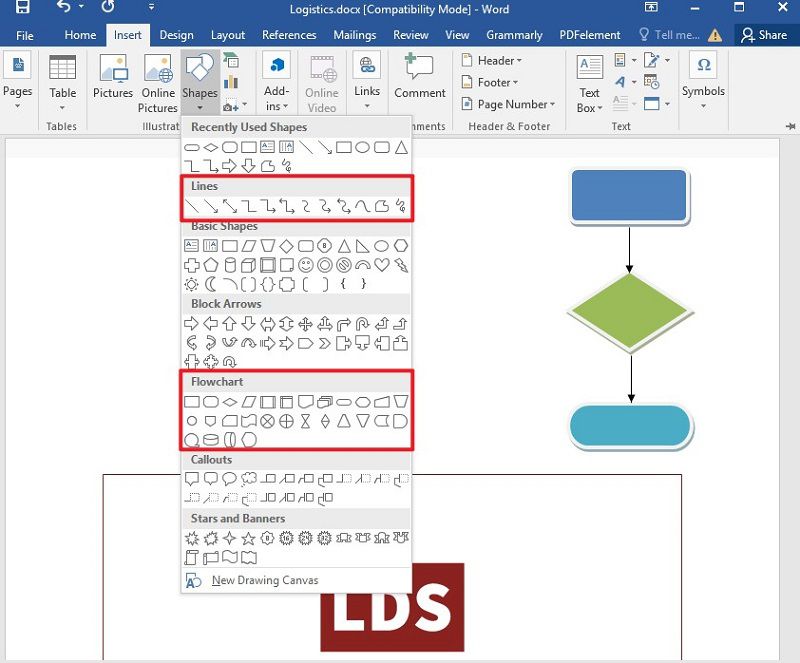
To create a workflow using Microsoft Word, you can use either SmartArt or Shapes from the Insert tab. Here are the steps to use Shapes for creating a flowchart:- Go to the Insert tab and click on Shapes.
- From the dropdown gallery, select a flowchart shape.
- Click anywhere in your document to add the shape.
- Continue adding shapes and lines to complete your flowchart.
- To add text to a shape, click on it and start typing. You can also right-click on the shape and choose Edit Text.
- To move a shape or line, click and drag it to a new location.
- To resize a shape, click and drag from a corner or edge and use the handle icon to rotate the shape.
- To change the design of your shapes, select your shape and click on the Format tab. From there, you can change the shape style, fill color, and outline color.
If you need to introduce different types of shapes to denote decisions, inputs, or some other common process steps, you can add the default rectangle shape and select it. From the right-click menu, choose Change Shape or click the Format tab and select Change Shape to choose a new shape type like a diamond or parallelogram.It's important to note that while Microsoft Word is not a diagramming program, it is still possible to add shapes and create flowcharts. By following these steps, you can create a simple flowchart in Microsoft Word to visualize your workflow or process. why is it hard to move the decision diamond of flowchart shape?
The decision diamond of a flowchart shape can be hard to move because it is often connected to multiple lines or arrows that represent different paths or outcomes. When you try to move the diamond, the lines may not move with it, or they may become disconnected from other shapes in the flowchart. This can make it difficult to maintain the correct sequence and layout of the flowchart. To avoid this problem, it is important to plan the flowchart carefully before adding shapes and lines. You should also use the correct symbol for each step, such as a diamond shape for decisions and rectangles for processes, and maintain consistent spacing between symbols. Additionally, some flowchart tools like SmartArt in Microsoft Word may not allow for easy creation of split paths after a decision, which can make it harder to move the decision diamond. tell me the easiest way to create flowcharts
There are several ways to create flowcharts, but the easiest way to create a flowchart in Microsoft Word is to use the built-in tools like SmartArt or Shapes. Here are the steps to create a flowchart using Shapes in Microsoft Word:- Open a new document in Microsoft Word.
- Go to the Insert tab and click on Shapes.
- From the dropdown gallery, select a flowchart shape.
- Click anywhere in your document to add the shape.
- Continue adding shapes and lines to complete your flowchart.
- To add text to a shape, click on it and start typing. You can also right-click on the shape and choose Edit Text.
- To move a shape or line, click and drag it to a new location.
- To resize a shape, click and drag from a corner or edge and use the handle icon to rotate the shape.
- To change the design of your shapes, select your shape and click on the Format tab. From there, you can change the shape style, fill color, and outline color.
If you prefer to use SmartArt, you can follow similar steps to create a flowchart. SmartArt provides a variety of graphic options to choose from, and you can always adjust, delete, or insert a new choice later. Once you have created your flowchart, you can save it as a Word document or export it as an image to share with others. tell me the easiest way to create flowcharts
The easiest way to create flowcharts is to use the built-in tools in Microsoft Word, such as SmartArt or Shapes. Here are the steps to create a flowchart using SmartArt:- Open a new document in Microsoft Word.
- Go to the Insert tab and click on SmartArt.
- From the dropdown gallery, select a flowchart style.
- Click on the shape you want to add and start typing to add text.
- To add a new shape, click on the existing shape and select the Add Shape button.
- To move a shape or line, click and drag it to a new location.
- To resize a shape, click and drag from a corner or edge and use the handle icon to rotate the shape.
- To change the design of your shapes, select your shape and click on the Design tab. From there, you can change the shape style, fill color, and outline color.
If you prefer to use Shapes, you can follow similar steps to create a flowchart. Shapes provide more flexibility in terms of shape types and layout, but may require more manual adjustments. Once you have created your flowchart, you can save it as a Word document or export it as an image to share with others. in asp.net mvc 5, what is the difference between session and [Authorize] can one be used in place on another?
Session and [Authorize] are two different concepts in ASP.NET MVC 5. Session is a server-side object that allows you to store and retrieve user-specific data across multiple requests. On the other hand, [Authorize] is an attribute that you can apply to a controller or action method to restrict access to authenticated users only.While both Session and [Authorize] can be used to control access to certain parts of an application, they serve different purposes. Session is typically used to store user-specific data, such as user preferences or shopping cart items, while [Authorize] is used to restrict access to certain parts of an application based on user roles or permissions.It is not recommended to use Session in place of [Authorize] or vice versa. Instead, you should use both Session and [Authorize] together to provide a secure and personalized user experience. For example, you can use Session to store user-specific data and [Authorize] to restrict access to certain parts of the application based on user roles or permissions.In summary, Session and [Authorize] are two different concepts in ASP.NET MVC 5 that serve different purposes. While both can be used to control access to certain parts of an application, they should be used together to provide a secure and personalized user experience. But isn't it possible than instead of Authorize I could check if a particular data in session exists say, I could store user's role, and userid in session when he logs in. So I could skip [Authorize] and just make use of session data?
Yes, it is possible to use Session data to check for authorization instead of using [Authorize] attribute in ASP.NET MVC 5. You can store user-specific data, such as user roles or permissions, in Session when the user logs in and then check for that data in subsequent requests to determine if the user is authorized to access certain parts of the application.However, it is important to note that using Session for authorization can be less secure than using [Authorize] attribute. Session data can be tampered with or hijacked by malicious users, whereas [Authorize] attribute provides a more secure and standardized way to restrict access to certain parts of the application.If you decide to use Session for authorization, you should take extra precautions to ensure the security of your application. For example, you can encrypt the Session data, use SSL to encrypt the communication between the client and server, and set a short expiration time for the Session data.In summary, while it is possible to use Session data to check for authorization in ASP.NET MVC 5, it may be less secure than using [Authorize] attribute. If you decide to use Session for authorization, you should take extra precautions to ensure the security of your application. "Session data can be tampered with or hijacked by malicious users, whereas [Authorize] attribute provides a more secure and standardized way to restrict access to certain parts of the application."
How?
Session data can be tampered with or hijacked by malicious users because it is stored on the server and can be accessed by anyone who has the session ID. Session hijacking is a technique used to take control of another user's session and gain unauthorized access to data or resources. Attackers can steal the session cookie or persuade the user to click a malicious link containing a prepared session ID to obtain the session ID. Once the attacker has the session ID, they can take over the session by using the same session ID for their own browser session.On the other hand, [Authorize] attribute provides a more secure and standardized way to restrict access to certain parts of the application. It restricts access to authenticated users only and can be used to restrict access based on user roles or permissions.In summary, Session data can be tampered with or hijacked by malicious users, whereas [Authorize] attribute provides a more secure and standardized way to restrict access to certain parts of the application by restricting access to authenticated users only and can be used to restrict access based on user roles or permissions. "ession data is stored on the server, and if not properly secured, it could be vulnerable to session hijacking or other security exploits. "
How??
Session data can be vulnerable to session hijacking or other security exploits if not properly secured. Session hijacking is a technique used to take control of another user's session and gain unauthorized access to data or resources. Attackers can steal the session cookie or persuade the user to click a malicious link containing a prepared session ID to obtain the session ID. Once the attacker has the session ID, they can take over the session by using the same session ID for their own browser session.To secure session data, it is recommended to encrypt session IDs and data using the database's inbuilt encryption routines. This protects against cases where a database backup is compromised. Additionally, session data should be stored in cookies on the user's machine, and the session details should be encrypted and sent as a secret to the user as a cookie. This means that on each request, there is decryption, which can slow down the user. It is also important to set a short expiration time for the Session data and use SSL to encrypt the communication between the client and server.In summary, session data can be vulnerable to session hijacking or other security exploits if not properly secured. To secure session data, it is recommended to encrypt session IDs and data, store session data in cookies on the user's machine, set a short expiration time for the Session data, and use SSL to encrypt the communication between the client and server. so if I understand correct, In the asp.net mvc 5, the server when a user logs in creates a cookie in which it stores the session ID. And this cookie is sent on each HTTP Request from the browser as an Idenitfier. Now, the attacker, if in some way is able to get his hands on the session cookie, can just copy the session cookie and start sending request with the victim user's cookie. Am I correct?
Yes, you are correct. In ASP.NET MVC 5, when a user logs in, the server creates a cookie that contains the session ID. This cookie is sent on each HTTP request from the browser as an identifier. If an attacker is able to get their hands on the session cookie, they can copy the session cookie and start sending requests with the victim user's cookie. This is known as session hijacking, and it can allow the attacker to take over the victim's session and gain unauthorized access to data or resources.To prevent session hijacking, it is recommended to encrypt the session data and use SSL to encrypt the communication between the client and server. Additionally, you can set a short expiration time for the session data and use HttpOnly and Secure flags for the session cookie. HttpOnly flag prevents client-side scripts from accessing the cookie, and Secure flag ensures that the cookie is only sent over HTTPS connections.In summary, session hijacking is a serious security threat that can occur if session data is not properly secured. To prevent session hijacking, it is recommended to encrypt the session data, use SSL, set a short expiration time for the session data, and use HttpOnly and Secure flags for the session cookie. but how does [Authorize] helps in this, that Session data doesn't?
The [Authorize] attribute helps in securing the application by restricting access to certain parts of the application based on user roles or permissions. It ensures that only authenticated users can access the authorized parts of the application. On the other hand, Session data is used to store user-specific data, such as user preferences or shopping cart items, and can be vulnerable to session hijacking or other security exploits if not properly secured.While Session data can be used to check for authorization, it may be less secure than using [Authorize] attribute. [Authorize] attribute provides a more secure and standardized way to restrict access to certain parts of the application by restricting access to authenticated users only and can be used to restrict access based on user roles or permissions.In summary, [Authorize] attribute helps in securing the application by restricting access to certain parts of the application based on user roles or permissions, while Session data is used to store user-specific data and can be vulnerable to session hijacking or other security exploits if not properly secured. but say if I copy the cookie which has the session ID of the logged in User.
How would [Authorize] prevent me from accessing the resource/action?
If an attacker copies the session cookie of a logged-in user, they can use that cookie to impersonate the user and gain access to the authorized parts of the application. However, if the application uses [Authorize] attribute, it restricts access to authenticated users only and can be used to restrict access based on user roles or permissions. This means that even if the attacker has the session cookie, they will not be able to access the authorized parts of the application without proper authentication and authorization.In summary, [Authorize] attribute helps in securing the application by restricting access to certain parts of the application based on user roles or permissions, even if the attacker has the session cookie. This ensures that only authenticated users can access the authorized parts of the application. "Therefore, the [Authorize] attribute will redirect you to the login page, even if you have the cookie with the session ID of the logged-in user."
Why though? What special thing does that attrbute checks? Doesn't it check the cookie as well? So?
The [Authorize] attribute checks whether the user is authenticated and authorized to access the requested resource or action. If the user is not authenticated, the attribute redirects the user to the login page. If the user is authenticated but not authorized, the attribute returns an HTTP 401 Unauthorized status code. This ensures that only authenticated and authorized users can access the authorized parts of the application.When a user logs in, the server creates a cookie that contains the session ID. This cookie is sent on each HTTP request from the browser as an identifier. If an attacker copies the session cookie of a logged-in user, they can use that cookie to impersonate the user and gain access to the authorized parts of the application. However, if the application uses [Authorize] attribute, it restricts access to authenticated users only and can be used to restrict access based on user roles or permissions. This means that even if the attacker has the session cookie, they will not be able to access the authorized parts of the application without proper authentication and authorization.In summary, [Authorize] attribute checks whether the user is authenticated and authorized to access the requested resource or action, and it ensures that only authenticated and authorized users can access the authorized parts of the application. This provides an additional layer of security to prevent unauthorized access, even if the attacker has the session cookie. Oh so you mean there are 2 cookies? One is having Auhtentication Ticket and one is storing session Id?
Yes, you are correct. The [Authorize] attribute checks the authentication ticket, which is stored in a cookie on the client-side, to determine if the user is authorized to access the requested resource or action. The authentication ticket contains information about the user, such as their roles or permissions, and is encrypted to prevent tampering. If the user is not authenticated, the attribute redirects the user to the login page. If the user is authenticated but not authorized, the attribute returns an HTTP 401 Unauthorized status code.In summary, the [Authorize] attribute checks the authentication ticket, which is stored in a cookie on the client-side, to determine if the user is authorized to access the requested resource or action. This provides an additional layer of security to prevent unauthorized access, even if the attacker has the session cookie. so say I am using FormAuthentication, then there is one cookie for that and one cookie for SessionID storage?
Yes, you are correct. When using FormsAuthentication in ASP.NET, there are two cookies that are used: one for the authentication ticket and one for the session ID. The authentication ticket cookie is used to store the encrypted authentication ticket, which contains information about the user, such as their roles or permissions. The session ID cookie is used to store the session ID, which is used to identify the user's session on the server.In summary, when using FormsAuthentication in ASP.NET, there are two cookies that are used: one for the authentication ticket and one for the session ID. The authentication ticket cookie is used to store the encrypted authentication ticket, while the session ID cookie is used to store the session ID. so how many cookies are really created?
The number of cookies created in ASP.NET depends on the application and its requirements. Typically, there are two cookies used in ASP.NET applications: one for the authentication ticket and one for the session ID. The authentication ticket cookie is used to store the encrypted authentication ticket, while the session ID cookie is used to store the session ID. However, an application can use more cookies to store additional data, such as user preferences or shopping cart items.The number of cookies that can be stored on the client-side depends on the browser and its limitations. Most browsers allow at least 300 cookies, at least 4096 bytes per cookie, and at least 20 cookies per unique host or domain name. However, actual cookie limitations vary from browser to browser. Each browser is limited by a per-domain cookie count and overall cookie size limit. what is the difference between
ASP.NET_SessionId cookie
and
.ASPXAUTH cookie
The ASP.NET_SessionId cookie and the .ASPXAUTH cookie are two different cookies used in ASP.NET applications. The ASP.NET_SessionId cookie is used to identify the user's session on the server, while the .ASPXAUTH cookie is used to determine if the user is authenticated (that is, has their identity been verified).The ASP.NET_SessionId cookie is created when the user first visits the website and is used to create a session between the user's browser and the server hosting the website. This cookie is then used to relate any subsequent requests to the said session.The .ASPXAUTH cookie is created when the user logs in and is used to store the encrypted authentication ticket, which contains information about the user, such as their roles or permissions. This cookie is used to determine if the user is authenticated and authorized to access the requested resource or action.In summary, the ASP.NET_SessionId cookie is used to identify the user's session on the server, while the .ASPXAUTH cookie is used to determine if the user is authenticated and authorized to access the requested resource or action. so if someone steals ASP.NET_SessionId and I have not used [Authorize] in my actions. They would easily be able to access the resources/actions?
But if I use [Authorize] it will also check authentication cookie ticket that is .ASPXAUTH s cookie and hence won't allow the access?
Am I CORRECT?
Yes, you are correct. If an attacker steals the ASP.NET_SessionId cookie and the application does not use [Authorize] attribute, the attacker would be able to access the resources/actions. However, if the application uses [Authorize] attribute, it will also check the authentication cookie ticket that is .ASPXAUTH cookie and hence won't allow the access. The .ASPXAUTH cookie is used to determine if the user is authenticated and authorized to access the requested resource or action.In summary, if an attacker steals the ASP.NET_SessionId cookie and the application does not use [Authorize] attribute, the attacker would be able to access the resources/actions. However, if the application uses [Authorize] attribute, it will also check the authentication cookie ticket that is .ASPXAUTH cookie and hence won't allow the access. BARDDSD
in asp.net mvc 5, what is the difference between session and [Authorize] can one be used in place on another?
Session is a server-side storage mechanism that allows you to store data about a user's session across multiple pages. This data is typically stored in a cookie that is sent to the user's browser and returned on each subsequent request.
[Authorize] is an ASP.NET MVC attribute that can be used to restrict access to controllers and actions based on a user's authentication status. The attribute can be configured to allow access only to users who are authenticated, users who are members of a specific role, or users who have a specific claim.
Key differences:
Session: Session data is stored on the server, while [Authorize] attributes are evaluated on each request.
Session: Session data can be accessed from anywhere in the application, while [Authorize] attributes are only applied to the controllers and actions that they are decorated with.
Session: Session data is typically used to store information about the user's current session, such as the items in their shopping cart or the page they were last viewing. [Authorize] attributes are typically used to restrict access to certain areas of the application based on the user's authentication status.
Can they be used in place of each other?
In general, no. Session data cannot be used to restrict access to controllers and actions in the same way that [Authorize] attributes can. However, there are some cases where you may want to use session data in conjunction with [Authorize] attributes. For example, you could use session data to store a flag indicating whether or not the user has already seen the login page. This flag could then be used in an [Authorize] attribute to prevent the user from seeing the login page again if they have already logged in.
Another example is if you have a controller that contains sensitive data. You could use an [Authorize] attribute to restrict access to the controller to users who are members of a specific role. You could then use session data to store the user's role information. This would allow you to avoid having to check the user's role membership on each request.
Best practices:
It is generally recommended to use [Authorize] attributes to restrict access to controllers and actions in ASP.NET MVC applications. This is because [Authorize] attributes are more secure and easier to maintain than using session data. However, there are some cases where you may want to use session data in conjunction with [Authorize] attributes.
If you do need to use session data, be sure to take steps to secure it. For example, you should encrypt the session data and use a strong session timeout.
profile picture
But isn't it possible than instead of Authorize I could check if a particular data in session exists say, I could store user's role, and userid in session when he logs in. So I could skip [Authorize] and just make use of session data?
1
Yes, it is possible to use session data instead of [Authorize] attributes to restrict access to controllers and actions in ASP.NET MVC. However, there are a few things to keep in mind:
Security: Session data is stored on the server, so it is vulnerable to attack if the server is compromised. [Authorize] attributes are evaluated on each request, so they are less vulnerable to attack.
Maintainability: It can be difficult to maintain code that uses session data to restrict access to controllers and actions. This is because you need to make sure that the session data is always up-to-date and that you are checking the session data in the correct places. [Authorize] attributes are easier to maintain because they are centralized in one place.
Here is an example of how to use session data to restrict access to a controller:
C#
public class HomeController : Controller
{
public ActionResult Index()
{
if (Session["UserId"] == null)
{
return RedirectToAction("Login", "Account");
}
// ...
}
}
Use code with caution. Learn more
This code will redirect the user to the login page if they do not have a valid user ID in their session.
Here is an example of how to use the [Authorize] attribute to restrict access to a controller:
C#
[Authorize]
public class HomeController : Controller
{
public ActionResult Index()
{
// ...
}
}
Use code with caution. Learn more
This code will only allow authenticated users to access the HomeController.
Overall, it is recommended to use [Authorize] attributes to restrict access to controllers and actions in ASP.NET MVC applications. However, there are some cases where you may want to use session data instead. If you do use session data, be sure to take steps to secure it.
Sources
github.com/unknown45/LaundryWebapp
profile picture
"ession data is stored on the server, and if not properly secured, it could be vulnerable to session hijacking or other security exploits. "
How??
Session data is vulnerable to session hijacking or other security exploits if it is not properly secured. This can happen in a number of ways, including:
Stealing the session cookie: An attacker can steal the session cookie from a victim's browser using a variety of methods, such as cross-site scripting (XSS) attacks, phishing attacks, or malware. Once the attacker has the session cookie, they can use it to impersonate the victim and access their account.
Predicting the session ID: An attacker can predict the next session ID that will be generated by the application. This can be done by analyzing the application's session generation algorithm or by exploiting a vulnerability in the application. Once the attacker has the next session ID, they can create their own session cookie and impersonate the victim.
Fixating the session ID: An attacker can force a victim's session ID to be fixed to a specific value. This can be done by tricking the victim into clicking on a malicious link or by exploiting a vulnerability in the application. Once the victim's session ID is fixed, the attacker can use it to impersonate the victim and access their account even after the victim has logged out.
To protect session data from session hijacking and other security exploits, you should take the following steps:
Use HTTPS: HTTPS encrypts all traffic between the browser and the server, which makes it much more difficult for attackers to steal session cookies.
Set a short session timeout: If a session is not used for a certain period of time, it should be automatically invalidated. This will help to prevent attackers from using stolen session cookies to access accounts.
Use a strong session ID generation algorithm: The session ID generation algorithm should be strong enough to resist prediction and brute force attacks.
Use session ID rotation: The session ID should be rotated at regular intervals. This will help to prevent attackers from fixating the session ID.
Use session validation: The application should validate the session ID on each request. This will help to prevent attackers from using invalid session cookies.
In addition to the above steps, you should also implement other security measures, such as input validation and cross-site scripting protection, to help protect your application from attack.
profile picture
so if I understand correct, In the asp.net mvc 5, the server when a user logs in creates a cookie in which it stores the session ID. And this cookie is sent on each HTTP Request from the browser as an Idenitfier. Now, the attacker, if in some way is able to get his hands on the session cookie, can just copy the session cookie and start sending request with the victim user's cookie. Am I correct?
Yes, that is correct. If an attacker is able to get their hands on a user's session cookie, they can impersonate that user and access their account. This is known as a session hijacking attack.
There are a number of ways that an attacker can steal a user's session cookie. For example, they could:
Use a cross-site scripting (XSS) attack to inject malicious code into a web page. This code could then be used to steal the user's session cookie.
Use a phishing attack to trick the user into entering their credentials on a fake website. The fake website could then steal the user's session cookie.
Use malware to infect the user's computer. The malware could then steal the user's session cookie.
Once the attacker has the user's session cookie, they can use it to send requests to the server on behalf of the user. This can allow them to access the user's account, perform actions on the user's behalf, or even steal sensitive data from the user's account.
To protect against session hijacking attacks, it is important to:
Use HTTPS to encrypt all communication between the browser and the server. This will make it more difficult for attackers to steal session cookies.
Set a short session timeout. This will limit the amount of time that an attacker can use a stolen session cookie to impersonate a user.
Use a strong session ID generation algorithm. This will make it more difficult for attackers to predict or brute-force session IDs.
Use session validation. This will help to ensure that session cookies are valid before they are used.
Educate users about the dangers of phishing attacks and malware.
By following these steps, you can help to protect your application from session hijacking attacks.
profile picture
but how does [Authorize] helps in this, that Session data doesn't?
The [Authorize] attribute helps to protect against session hijacking attacks by authenticating the user on each request. This is in contrast to session data, which is stored on the server and is only checked on the first request.
If an attacker steals a user's session cookie, they will only be able to access the user's account if the [Authorize] attribute is not used. If the [Authorize] attribute is used, the attacker will be redirected to the login page when they try to access the user's account.
The [Authorize] attribute also helps to protect against other types of attacks, such as brute force attacks and replay attacks.
Here are some of the benefits of using the [Authorize] attribute:
It is more secure than using session data.
It is easier to maintain.
It can be used to protect controllers and actions based on the user's authentication status, role membership, and claims.
Overall, it is recommended to use the [Authorize] attribute to protect controllers and actions in ASP.NET MVC applications.
Here are some additional tips for protecting against session hijacking attacks:
Use a strong session ID generation algorithm.
Set a short session timeout.
Use session rotation.
Implement cross-site scripting (XSS) protection.
Implement input validation.
Educate users about the dangers of phishing attacks and malware.
profile picture
"If an attacker steals a user's session cookie, they will only be able to access the user's account if the [Authorize] attribute is not used. If the [Authorize] attribute is used, the attacker will be redirected to the login page when they try to access the user's account."
Why?
The [Authorize] attribute works by checking the user's authentication status on each request. If the user is not authenticated, the attribute will redirect the user to the login page.
Session data, on the other hand, is only checked on the first request. This means that if an attacker steals a user's session cookie, they will be able to access the user's account even if the user has logged out.
The [Authorize] attribute is more secure than session data because it authenticates the user on each request. This makes it more difficult for attackers to impersonate users and access their accounts.
Here is an example of how to use the [Authorize] attribute to protect a controller:
C#
[Authorize]
public class HomeController : Controller
{
public ActionResult Index()
{
// ...
}
}
Use code with caution. Learn more
This code will only allow authenticated users to access the HomeController. If an attacker tries to access the HomeController without being authenticated, they will be redirected to the login page.
It is important to note that the [Authorize] attribute is not a silver bullet. It is still important to take other security measures, such as using HTTPS, setting a short session timeout, and implementing XSS protection. However, the [Authorize] attribute is a valuable tool for helping to protect your application from session hijacking attacks.
profile picture
but say if I copy the cookie which has the session ID of the logged in User.
How would [Authorize] prevent me from accessing the resource/action?
The [Authorize] attribute prevents you from accessing the resource/action because it checks the user's authentication status on each request. When you copy the cookie with the session ID of the logged-in user, you are not authenticated. Therefore, the [Authorize] attribute will redirect you to the login page.
Here is a more detailed explanation of how the [Authorize] attribute works:
The [Authorize] attribute checks to see if the user is authenticated.
If the user is not authenticated, the attribute redirects the user to the login page.
If the user is authenticated, the attribute checks to see if the user has the necessary permissions to access the resource/action.
If the user does not have the necessary permissions, the attribute redirects the user to the access denied page.
If the user has the necessary permissions, the attribute allows the user to access the resource/action.
In your case, you are not authenticated because you copied the cookie with the session ID of the logged-in user. Therefore, the [Authorize] attribute will redirect you to the login page, even if you have the cookie with the session ID of the logged-in user.
To prevent session hijacking attacks, it is important to use the [Authorize] attribute to protect all resources/actions that require authentication. You should also use HTTPS to encrypt all communication between the browser and the server, set a short session timeout, and implement XSS protection.
profile picture
"Therefore, the [Authorize] attribute will redirect you to the login page, even if you have the cookie with the session ID of the logged-in user."
Why though? What special thing does that attrbute checks? Doesn't it check the cookie as well? So?
The [Authorize] attribute does check the cookie, but it also checks the user's authentication status. The user's authentication status is stored in the database, not in the cookie.
When a user logs in, the application creates a session and stores the session ID in the cookie. The session ID is used to track the user's session across multiple requests.
The [Authorize] attribute checks the session ID in the cookie to see if the user has a valid session. If the user has a valid session, the attribute then checks the user's authentication status in the database. If the user is authenticated, the attribute allows the user to access the resource/action.
If the user does not have a valid session or if the user is not authenticated, the attribute redirects the user to the login page.
This is why the [Authorize] attribute can prevent you from accessing the resource/action even if you have the cookie with the session ID of the logged-in user.
Here are some examples of when the [Authorize] attribute would redirect you to the login page:
You copy the cookie with the session ID of the logged-in user, but you are not authenticated.
The user's session has expired.
The user has logged out.
The user's account has been disabled.
The user does not have the necessary permissions to access the resource/action.
The [Authorize] attribute is a valuable tool for helping to protect your application from session hijacking attacks and other security exploits.
profile picture
Oh so you mean there are 2 cookies? One is having Auhtentication Ticket and one is storing session Id?
Yes, there are two cookies: one for the authentication ticket and one for the session ID.
The authentication ticket contains information about the user, such as their username and role membership. It is encrypted and signed to prevent tampering.
The session ID is used to track the user's session across multiple requests. It is not encrypted, but it is typically set to expire after a short period of time.
Both cookies are created when a user logs in. The authentication ticket is stored in the browser's cache, while the session ID is stored in the browser's cookie jar.
On each subsequent request, the browser sends the authentication ticket and session ID to the server. The server uses the authentication ticket to verify the user's identity. The server uses the session ID to track the user's session and to ensure that the user is authorized to access the resources they are requesting.
The [Authorize] attribute checks the authentication ticket to verify the user's identity. It also checks the user's role membership to ensure that the user is authorized to access the resources they are requesting.
By using two cookies, the ASP.NET MVC framework is able to provide a secure and efficient way to authenticate users and track their sessions.
profile picture
so say I am using FormAuthentication, then there is one cookie for that and one cookie for SessionID storage?
Yes, that is correct. If you are using Forms Authentication, then there is one cookie for the Forms Authentication ticket and one cookie for the session ID.
The Forms Authentication ticket is encrypted and contains information about the user, such as their username and role membership. The session ID is not encrypted and is used to track the user's session across multiple requests.
Both cookies are created when a user logs in. The Forms Authentication ticket is stored in the browser's cache, while the session ID is stored in the browser's cookie jar.
On each subsequent request, the browser sends the Forms Authentication ticket and session ID to the server. The server uses the Forms Authentication ticket to verify the user's identity. The server uses the session ID to track the user's session and to ensure that the user is authorized to access the resources they are requesting.
The [Authorize] attribute checks the Forms Authentication ticket to verify the user's identity. It also checks the user's role membership to ensure that the user is authorized to access the resources they are requesting.
By using two cookies, Forms Authentication is able to provide a secure and efficient way to authenticate users and track their sessions.
Here is a diagram that shows how Forms Authentication works:
[Diagram of Forms Authentication workflow]
The user enters their credentials on the login page.
The server authenticates the user and creates a Forms Authentication ticket.
The server encrypts the Forms Authentication ticket and sends it to the browser in a cookie.
The browser stores the Forms Authentication ticket in its cache.
On each subsequent request, the browser sends the Forms Authentication ticket to the server in a cookie.
The server decrypts the Forms Authentication ticket and uses it to verify the user's identity.
The server authorizes the user to access the resources they are requesting.
Forms Authentication is a powerful and flexible authentication system that can be used to protect any ASP.NET MVC application.
profile picture
so how many cookies are really created?
The number of cookies created in ASP.NET MVC depends on a number of factors, including the type of authentication you are using and whether you are using any third-party libraries or frameworks.
In general, the following cookies are created:
FormsAuthentication cookie: This cookie is created when a user logs in using Forms Authentication.
SessionID cookie: This cookie is created when a user starts a session.
ASP.NET_SessionId cookie: This cookie is created by ASP.NET to track the user's session.
.ASPXAUTH cookie: This cookie is created by ASP.NET to store the user's authentication ticket.
In addition to these cookies, third-party libraries and frameworks may also create their own cookies.
For example, if you are using the ASP.NET Identity framework, then the following additional cookies may be created:
.AspNet.ApplicationCookie: This cookie is used by ASP.NET Identity to store the user's authentication ticket.
.AspNet.CorrelationCookie: This cookie is used by ASP.NET Identity to track the user's session.
.AspNet.xsrfToken: This cookie is used by ASP.NET Identity to prevent cross-site request forgery (CSRF) attacks.
The number of cookies created can vary depending on your specific configuration. For example, if you are using a single sign-on (SSO) solution, then additional cookies may be created.
If you are concerned about the number of cookies being created, you can try the following:
Use a third-party cookie management tool to manage and control the cookies that are created.
Configure your application to use fewer cookies. For example, you can configure Forms Authentication to use a single cookie for both the authentication ticket and the session ID.
Use a content delivery network (CDN) to serve static content, such as images and JavaScript files. This can reduce the number of cookies that are created because the CDN will serve the static content from its own servers.
It is important to note that some cookies are necessary for the proper functioning of your application. For example, the .ASPXAUTH cookie is necessary for Forms Authentication to work. Therefore, it is important to carefully consider the impact of any changes you make to the cookies that are created.
profile picture
so if someone steals ASP.NET_SessionId and I have not used [Authorize] in my actions. They would easily be able to access the resources/actions?
But if I use [Authorize] it will also check authentication cookie ticket that is .ASPXAUTH s cookie and hence won't allow the access?
Am I CORRECT?
View other drafts
Yes, you are correct. If someone steals the ASP.NET_SessionId cookie and you have not used the [Authorize] attribute in your actions, they will be able to access the resources/actions. However, if you use the [Authorize] attribute, it will also check the authentication cookie ticket (.ASPXAUTH cookie) and will not allow the access.
The [Authorize] attribute works by checking the user's authentication status on each request. If the user is not authenticated, the attribute redirects the user to the login page.
The ASP.NET_SessionId cookie is used to track the user's session across multiple requests. If an attacker steals the ASP.NET_SessionId cookie, they can impersonate the user and access their account.
The .ASPXAUTH cookie contains the user's authentication ticket. This ticket is encrypted and contains information about the user, such as their username and role membership.
When you use the [Authorize] attribute, it checks the .ASPXAUTH cookie to verify the user's identity. If the user is not authenticated, the attribute redirects the user to the login page.
Therefore, if you use the [Authorize] attribute, it will protect your application from session hijacking attacks, even if an attacker steals the ASP.NET_SessionId cookie.
In addition to using the [Authorize] attribute, there are a number of other things you can do to protect your application from session hijacking attacks, such as:
Use HTTPS to encrypt all communication between the browser and the server.
Set a short session timeout.
Use session rotation.
Implement cross-site scripting (XSS) protection.
Implement input validation.
Educate users about the dangers of phishing attacks and malware.
By following these tips, you can help to protect your application from session hijacking attacks and other security exploits.